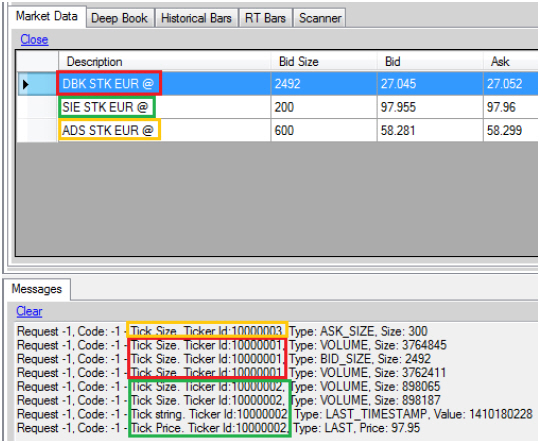
SMArc: A Proposal for a Smart, Semantic Middleware Architecture Focused on Smart City Energy Management - Jesús Rodríguez-Molina, José-Fernán Martínez, Pedro Castillejo, Rubén de Diego, 2013

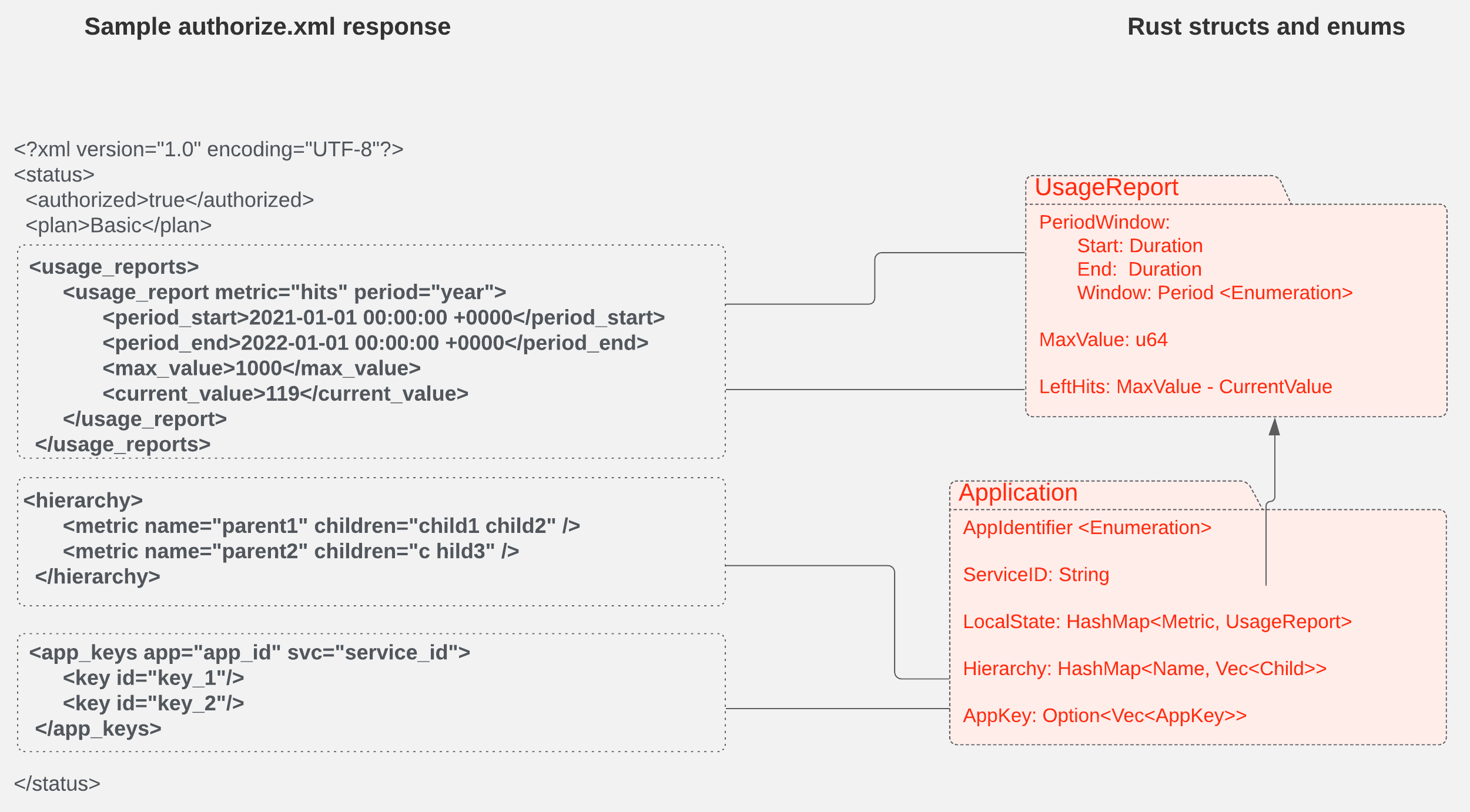
Electronics | Free Full-Text | Virtualization Based Efficient Service Matching and Discovery in Internet of Things